Sep
24
2011
You can’t wait to install Windows server 8 developer preview in order to test it in the event of a future deployment… But you might want to finish your migration to ADDS 2008R2 before thinking about all that 😉 Bellow is a tab showing some client compatibility issues and the important steps when migrating your domain controllers to Windows server 2008R2:
Read more »
Sep
08
2011
This article describes how to digitally sign an Excel VBA project with a certificate issued by your ADCS PKI. You can use the same method to sign any Office VBA project but in this post we will focus on Excel. For an introduction on how to sign Office macros you can read these KB and MSDN articles.
Read more »
May
31
2011
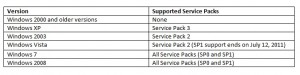
In this post we will describe how to make a WSUS clients inventory, we will search for the computers in your domain which are not able to receive MS security updates because they are not supported any more or because there is a misconfinguration on the WSUS client. Below is a tab listing supported OS and Service Packs versions:
Read more »
Apr
29
2011
We will show in this post how to create a SAN certificate for IIS 7 using an Enterprise PKI. This kind of certificate permits you to host multiple SSL sites on a single server. To achieve this with a powershell script we will use the PSRemoting and the IIS CmdLets.
We launch the script from the server where we administrate the PKI with ADCS RSAT. We will use PSRemoting for many things: Before sending the certificate request to the Certificate Authority in order to create the CSR on the IIS server. Once the certificate is issued we will retrieve it and install it to the IIS 7 server certificate store. Finally we will configure IIS 7 to use this certificate on the default web site.
Read more »
Jan
06
2011
In order to edit GPO permissions with Powershell you can use the Set-GPPermissions CmdLet shipped with the RSAT (import-module grouppolicy). This Cmdlet does not have a replace permission option, nor does it let you set up a deny ACE on a GPO. In this post we will explain how to replace permissions on a GPO object thanks to the Security Descriptor Definition Language. This language is used to edit permissions in string format on all kind of objects (file system, registry, AD objects…). For a better understanding of the SDDL and a tool that translates a SDDL string you can read this post.
When do you need to replace permissions on a GPO? When an “OU administrator” account which is a member of the “OU administrators” group creates a GPO (and links it to an OU of his site), he is the owner of this object, members of the “domain admins” group can edit this GPO, but members of the“OU administrators” group cannot. So you might want to edit your GPO’s security settings by replacing the “OU administrator” account which created the GPO with the group that includes all the “OU administrators”. In our example, the domain has two sites, each one represented by an OU, we have two types of GPOs: Read more »
Sep
06
2010
When you install Windows 2008 Certification Authority a new domain controller certificate template named Kerberos Authentication is available. It replaces the Domain Controller Authentication template. If you need more information about the new certificate templates shipped with a Windows 2008 CA you can read this article.
Here is a tab that outlines the specific attributes of the Domain Controller Authentication and Kerberos Authentication templates:
| |
Domain Controller Authentication |
Kerberos Authentication |
| Key Usage |
Client Authentication
Server Authentication
Smart Card Logon |
Client Authentication
Server Authentication
Smart Card Logon
KDC Authentication. |
| Subject Alternate Name |
DNS Name : Domain Controller FQDN. |
DNS Name : Domain FQDN.
DNS Name : Domain NetBios name. |
Read more »
Aug
07
2010
You might already know that Windows 2000 and XP SP2 are not supported by MS since the 13th of july 2010. As a consequence you cannot install new security patches released by MS on these platforms. A critical security vulnerability MS10-46 is corrected by the KB2286198 patch which was released the 3rd of august. This patch applies at least to Windows XP SP3 (for workstation versions) and Windows 2003 SP2 (for server versions). The KB article explains a workaround for the security patch, you need to edit two registry keys and disable a service.
You can apply this workaround on earlier version of Windows, if all your computers are not up to date. The disavdantage of this method is that icon images will disappear on some of your *.lnk files. So my advice is to upgrade as soon as possible your computers to a version which is supported by MS and apply the official security patch. Use the workaround only as last resort, the purpose of this post is to show you how to deploy this workaround with a GPO and play with WMI filtering. The Group Policy Center already wrote an article on how to deploy this workaround with GPO. We will just show you in this post how to target more precisely your computers which need the workaround by using WMI filers. We will achieve this under Windows 2008 by using Group Policy Preferences and activate the GPO workaround on the computers which have not the KB2286198 security patch installed. And we will show you how to achieve the same thing under AD 2003, without using Group Policy Preferences.
Read more »
May
12
2010
With restricted group policies you can define the content of the local groups on your workstations and servers. Thanks to these GPOs you can set up which domain groups will be local administrators, power users, remote desktop users etc. on the PCs.
If you want more details about restricted group policies and can understand French I suggest you read Jonathan’s post on the Portail MCSE blog. If you only understand English you will find a description here. You can use the “Members” portion of restricted group policy, which we will call “replace mode restricted group policy” or the “Member Of” portion of restricted group policy, which we will call “add mode restricted group policy”. This feature is supported on Windows 2000 SP4 and later versions.
In this article we will focus on setting up a replace mode restricted group policy that modifies the local administrator and power users group on our workstations.
Read more »
May
09
2010
We will describe in this post how to secure your autologon workstations. Those PCs are accessed by everyone inside your company because no account and password are required to login.This is why you need to work out how to secure them.
The autologon workstation uses a service user account to open a windows session, the most obvious way to set up an autologon on a workstation is to edit registry keys. This method is not secure because the account credentials appear in clear text in the registry, meaning that the account can easily be used for other purpose.
Read more »
Apr
18
2010
The title of this post seems a bit contradictory, the use of generic accounts in your domain should be limited to the minimum. Access to your domain ressources should be done with nominative accounts when possible, that’s why you want to avoid generic accouns use. However for political or historical reasons a department of your company might use this type of accounts to access some applications or log on some computers. This account is used by several persons, accordingly the password does not remain secret and across many departments, non-authorized persons might know it and use it for other purposes. If you set up a classic change password policy for this account, then when the password expires, a single person will change it and will probably not notify other users that are entitled to use the account of the new password. That’s why generic accounts are generally flagged “the password never expires”, which is an obvious lack of security. We will demonstrate in this post how to set up an automatic system that will change the password and notify users entitled to use the account.
Read more »

