Windows 8: Install and configure ADCS
We will describe in this post how to install ADCS on Windows 8 Developer Preview, and how to configure your PKI with Powershell.
Firstly we will install the ADCS role with Server Manager:
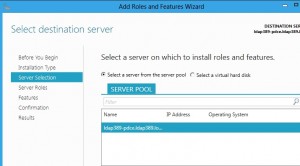
Select “Role-based installation or Feature-based installation” and click next. We now need to select the server on which you will install the role, under Windows 8 you can manage a remote server 🙂
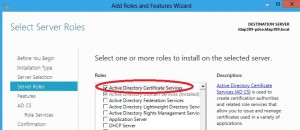
Choose the Active Directory Certificate Services role:
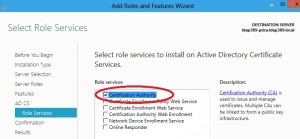
Skip the Features screen, then under the role services screen, select only Certification Authority:
On the next screen we start the role installation. Once it is done, open a Powershell session on the server on which the role is installed and launch the following command:
Get-Module –ListAvailable |
We notice that a new module called CertificateServicesCmdlets shows up. We can list the cmdlets available in that module with the command:
(get-module CertificateServicesCmdlets).exportedcommands |
Here are the cmdlets:
Get-AdcsCertificationAuthorityConfigurationDefaults
Get-AdcsConfigurationState
Get-AdcsEnrollmentPolicyWebServiceConfigurationDefaults
Get-AdcsEnrollmentWebServiceConfigurationDefaults
Get-AdcsNetworkDeviceEnrollmentConfigurationDefaults
Get-SSLCertificates
Import-AdcsCertificationAuthorityCACertificatePfx
Install-AdcsCertificationAuthority
Install-AdcsEnrollmentPolicyWebService
Install-AdcsEnrollmentWebService
Install-AdcsNetworkDeviceEnrollmentService
Install-AdcsOnlineResponder
Install-AdcsWebEnrollment
Uninstall-AdcsCertificationAuthority
Uninstall-AdcsEnrollmentPolicyWebService
Uninstall-AdcsEnrollmentWebService
Uninstall-AdcsNetworkDeviceEnrollmentService
Uninstall-AdcsOnlineResponder
Uninstall-AdcsWebEnrollment
We will use the Install-AdcsCertificationAuthority in order to configure our Enterprise rootCA server. The script setupCA.vbs inspired us to launch the following command:
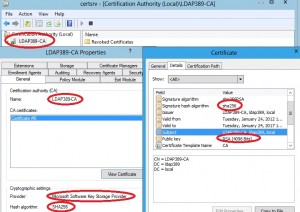
Install-AdcsCertificationAuthority -CAType EnterpriseRootCA -CACommonName LDAP389-CA -KeyLength 4096 -HashAlgorithmName SHA256 -CryptoProviderName "RSA#Microsoft Software Key Storage Provider" |
Here we go, the Enterprise rootCA server is ready to use. We launch the Certification Authority console in order to check that the configuration matches the parameters we set up with Powershell:
Under Windows 8 you can configure your PKI with Powershell, but maybe not yet get rid of the excellent PS PKI module developed by the Powershell Crypto Guy, time will tell…
N.B.: As it is a Developer Preview the cmdlets and installation procedure might change in the future.
This post is also available in: French