Powershell: Use GPO to configure firewall settings
In this post we will set up firewall rules using Group Policy Objects under Windows 2008 Server. When you install a windows role or feature the installer will configure firewall rules automatically upon installation. Some third party installers reconfigure the default Windows Firewall port settings and no further configuration is needed (e.g. Xenapp 5.0 for Windows 2008 to allow incoming connections, such as those from ICA traffic and the IMA service), some others don’t… For those applications we will configure the firewall rules and import those settings into an existing GPO with the netsh advfirewall command.
Firstly you need to find out the inbound and outbound firewall rules to ensure your application will function properly by editing the local firewall rules on a test server. Those rules we will be named with a given prefix ($prefix=LDAP389 in this example). Secondly we export the firewall rules in a wfw configuration file ($wfwfile) with the following command:
netsh advfirewall export $wfwfile
Then we need to import the firewall rules with the name beginning: $prefix=LDAP389 into a GPO ($GPONAME), in order to apply these settings to all the servers that need this specific firewall configuration.
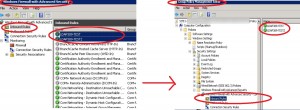
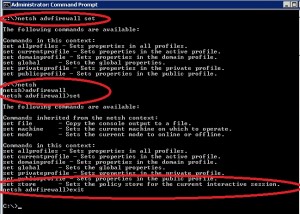
In order to import these settings you use the netsh advfirewall command and connect to the GPO store. Unfortunatly the “netsh advfirewall set store gpo=domain\gpo_name” does not seem to work when used as a oneliner, you must first be in the advfirewall context in order to use the set store command.
To achieve a successful import of the wfw file into the GPO use the following code, thanks for the tip VMdude 🙂
$stream = [System.IO.StreamWriter] $netshinput $stream.WriteLine('advfirewall') $stream.WriteLine('set store gpo=' + $domainfqdn + '\' + $GPONAME) $stream.WriteLine('show store') $stream.WriteLine('import ' + $wfwfile) $stream.WriteLine('exit') $stream.close() get-content $netshinput | netsh |
Now all the firewall rules you configured on your test server are imported into the GPO, including the default Windows firewall rules. You may want to keep only the rules where the name begins with $prefix=LDAP389, firstly because too many parameters in a GPO might slow down group policy processing, secondly because the GPO settings tab will be more easy to read. We will use the Remove-GPRegistryValue CmdLet to delete all the inbound and outbound rules which name does not begin with $prefix=LDAP389.
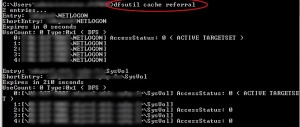
Before deleting these settings we must retrieve the Domain Controller ($bindserver) on which the netsh advfirewall edited the GPO, for that you need to know the active targetset for the SYSVOL share:
In order to retrieve the $bindserver value, use the following code:
$dfs = dfsutil cache referral foreach ($dfss in $dfs) {if (($dfss -like '*ACTIVE TARGETSET*') -and ($dfss -like '*sysvol*')) { $bindserver = $dfss.split("\")[1]}} |
Now you will be working with your GPO CmdLets on the same DC the netsh advfirewall did. This will avoid any replication issues. You just need to retrieve the firewall rules with names that do not begin with $prefix=LDAP389 and delete these rules:
# Get GPO reg settings for FW rules $gporeg = get-GPRegistryValue -Name $GPONAME -server $bindserver -Key "HKLM\SOFTWARE\Policies\Microsoft\WindowsFirewall\FirewallRules" # Remove FW rules which do not match $prefix* foreach ($gporegs in $gporeg) { if ($gporegs.Value -notlike '*Name=' + $prefix + '*') {Remove-GPRegistryValue -Name $GPONAME -server $bindserver -key "HKLM\SOFTWARE\Policies\Microsoft\WindowsFirewall\FirewallRules" -ValueName $gporegs.ValueName} } |
You can download the full script here:
You just need to change the following values:
- $prefix: Prefix of the firewall inbound and outbound rules you want to keep in your GPO.
- $GPONAME: Name of the GPO you want to import the settings into.
This post is also available in: French