GPO WMI filtering: KB2286198 workaround
You might already know that Windows 2000 and XP SP2 are not supported by MS since the 13th of july 2010. As a consequence you cannot install new security patches released by MS on these platforms. A critical security vulnerability MS10-46 is corrected by the KB2286198 patch which was released the 3rd of august. This patch applies at least to Windows XP SP3 (for workstation versions) and Windows 2003 SP2 (for server versions). The KB article explains a workaround for the security patch, you need to edit two registry keys and disable a service.
You can apply this workaround on earlier version of Windows, if all your computers are not up to date. The disavdantage of this method is that icon images will disappear on some of your *.lnk files. So my advice is to upgrade as soon as possible your computers to a version which is supported by MS and apply the official security patch. Use the workaround only as last resort, the purpose of this post is to show you how to deploy this workaround with a GPO and play with WMI filtering. The Group Policy Center already wrote an article on how to deploy this workaround with GPO. We will just show you in this post how to target more precisely your computers which need the workaround by using WMI filers. We will achieve this under Windows 2008 by using Group Policy Preferences and activate the GPO workaround on the computers which have not the KB2286198 security patch installed. And we will show you how to achieve the same thing under AD 2003, without using Group Policy Preferences.
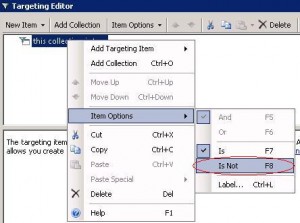
First, we will show you how to apply the Group Policy Center workaround by targeting only computers which have not the security patch installed. For this we will use Item-Level targeting. If you want to use Group Policy Preferences you need at least a DC running Windows 2008 in your domain and apply this KB on all your client computers, do not forget to install XMLLite on computers running Windows 2003 and Windows XP. One of the cool features about Item-Level targeting is Targeting Collection: You can add a “IS NOT” statement in your filter (i.e. request result is FALSE). With standard WMI filtering (i.e. not using Group policy Preference) you just can filter if the request returns TRUE, so you cannot filter if a KB is not installed, just if a KB is installed. In order to deploy the workaround on computers which have not KB2286198 installed just add Item-Level targeting on the registry key update and service deactivation:
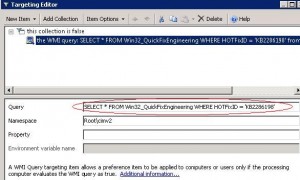
The WMI request to retrieve if KB patch is installed browses the Win32_QuickFixEngineering class by filtering on HotFixID = ‘KB2286198’.
In order to disable the workaround just use the same WMI request and use default Targeting Collection, which applies if WMI filter returns TRUE. See part “disable workaround” in the Group Policy Center post, to know which registry key and WebClient settings to edit.
If your AD is still running with just Windows 2003 DCs, you cannot use Group Policy Preferences and a WMI filter only applies if the request returns TRUE, which is the standard behaviour. In order to bypass this limitation it is a bit tricky: We will create two GPOs and we will apply them in a particular order (priority):
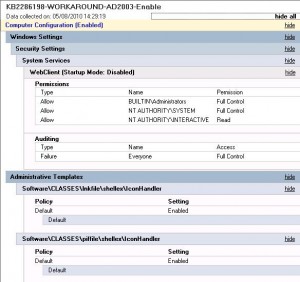
- First GPO (KB2286198-WOKAROUND-AD2003-Enable) which will enable the workaround on all your workstations (no filtering): It will disable the WebClient Service and edit registry keys HKCR\lnkfile\shellex\IconHandler et HKCR\piffile\shellex\IconHandler and HKCR\lnkfile\shellex\IconHandler with a void default value. When the computer processes Group Policy, KB2286198-WOKAROUND-AD2003-Enable will be applied before the second GPO, so it’s priority will be lower.
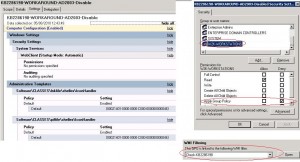
- Second GPO (KB2286198-WOKAROUND-AD2003-Disable) which will disable the workaround on workstations with KB2286198 installed, by using a standard WMI filter. This GPO enables WebClient service at startup and edit the registry default value to its original setting ({00021401-0000-0000-C000-000000000046}). This GPO will have a higher priority than the first one, it will be applied after KB2286198-WOKAROUND-AD2003-Enable during the computer’s group policy processing.
In order to push the registry values mentioned earlier, without Group Policy preference, you will need to generate a custom administrative template with Yizhar Hurwitz’s tool: Reg2adm.If you need a tutorial on how to use it you can read this post. Otherwise if you just want to download both .ADM files just click on the image below:
The WMI filter you need to apply on the second GPO KB2286198-WOKAROUND-AD2003-Disable is still the same as under Windows 2008:
SELECT * FROM Win32_QuickFixEngineering WHERE HOTFixID = ‘KB2286198’
If you still (!) have Windows 2000 workstations and servers in you domain they will ignore the WMI filter. The GPO KB2286198-WOKAROUND-AD2003-Disable will always be applied to those computers, but you need to apply the workaround to them because the security patch cannot be installed on a W2K OS.
We will create a security group called W2K-WORKSTATIONS whose members are all our Windows 2000 computers. For that we will use Quest AD CMDlets and launch the following command:
get-QADComputer -OSName 'Windows 2000*' -ldapFilter '(!(userAccountControl:1.2.840.113556.1.4.803:=2))' -Sizelimit 10000 | Add-QADMemberof -Group 'ldap389\W2K-WORKSTATIONS' |
Then we will set up a group security filtering on the GPOKB2286198-WOKAROUND-AD2003-Disable in order to deny its application for the W2K-WORKSTATIONS group.
The GPO KB2286198-WOKAROUND-AD2003-Enable looks like this:
And GPO KB2286198-WOKAROUND-AD2003-Disable with an higher priority than KB2286198-WOKAROUND-AD2003-Enable looks like this (WMI + security filtering):
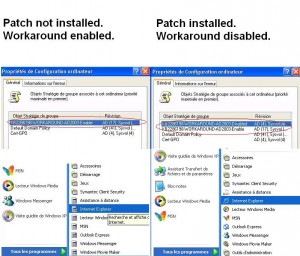
On the image bellow is the startup menu and the resultant set of policy on a computer with KB2286198 installed and on a computer with workaround applied:
By using GPO processing order we can achieve what we want but it is a bit makeshift… As a conclusion keep your OS updated, in the future there might be no simple workarounds to halt a critical security breach
This post is also available in: French