Restricted groups policy
With restricted group policies you can define the content of the local groups on your workstations and servers. Thanks to these GPOs you can set up which domain groups will be local administrators, power users, remote desktop users etc. on the PCs.
If you want more details about restricted group policies and can understand French I suggest you read Jonathan’s post on the Portail MCSE blog. If you only understand English you will find a description here. You can use the “Members” portion of restricted group policy, which we will call “replace mode restricted group policy” or the “Member Of” portion of restricted group policy, which we will call “add mode restricted group policy”. This feature is supported on Windows 2000 SP4 and later versions.
In this article we will focus on setting up a replace mode restricted group policy that modifies the local administrator and power users group on our workstations.
Setting up this kind of GPO requires making an inventory of your computers: You have to know precisely which users have elevated rights on their PCs. Taking away these rights overnight might cause tension, in addition to technical problems that will occur… In order to retrieve users with those privileges you can use the trial version of Exporter Pro for 30 days, you can also use the command line freeware version, or you can set up your own inventory script.
Once you have a complete list of the domain users which have local administrator or power user privileges on their workstation you have to know why:
- Political reasons: That’s the way it is and it won’t change… You will not apply the replace mode restricted group policy on his workstation, you will apply the add mode restricted group policy.
- A Software installed on the PC needs elevated rights to run correctly.
- No particular reason : The replace mode restricted group policy will be applied on this workstation.
The second scenario is the one that needs an investigation: Usually an application does not need to have elevated rights to run properly, you just need to grant write permission on some folders, files and registry keys.
Our job will be to identify objects on which you need to grant write permissions for our application to run: The first thing to do is ask the software company, they certainly have this kind of information. Otherwise we will have to track files and registry keys our program tries to access by using Process Monitor. We will show how to perform this operation by studying Tun Plus 10.0.1 developed by Esker.
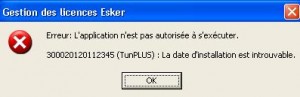
This application runs after the user logs on, the command “C:\Program Files\TUN\tcpw\walld32.exe -h” is launched. When you log on with a standard user account you have this error message:
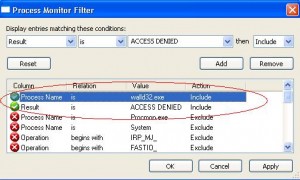
We will identify what folders, files and registry keys the walld32.exe needs to have write access on. In your standard user session runas a local administrator the procmon.exe program. Start the capture, launch the walld32.exe -h and the error message should be displayed, stop the Process Monitor capture. Create a filter in order to retrieve denied access of the process walld32.exe:
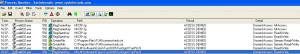
Our standard user account is trying to write on the following registry keys and folders:
On the workstations where the Tun Plus software is installed you have to grant standard users the appropriate rights on the registry keys and folder. Before applying the replace mode restricted group policy you have to create a GPO that grants standard users the necessary rights on their computers. If your Tun Plus computers are located in the same OU as other computer objects you will need to apply security filtering so as not to grant the privileges on other workstations.
Rather than granting rights on the file system or registry to a user, you can also elevate privileges for an application (i.e. one or more processes) by using Privilege Authority edited by ScriptLogic.
Once you are done with this application inventory you can apply the replace mode restricted groups policy to almost all your computers. However you must ensure one last thing: That your users are owners of their profile. If the local administrators group owns the profile, former members of the administrator group downgraded to standard users may be surprised, as described in Jonathan’s post.
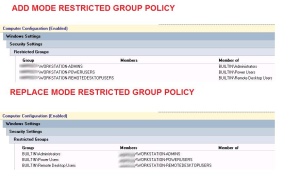
For the users that will retain elevated privileges on their workstations we will apply the add mode restricted group policy. Here is a screenshot of the replace and add mode GPOs:
You can change these GPOs to match your needs, you can add some local groups (e.g. Print Operators…), and choose the GPO mode you want to apply.
This post is also available in: French